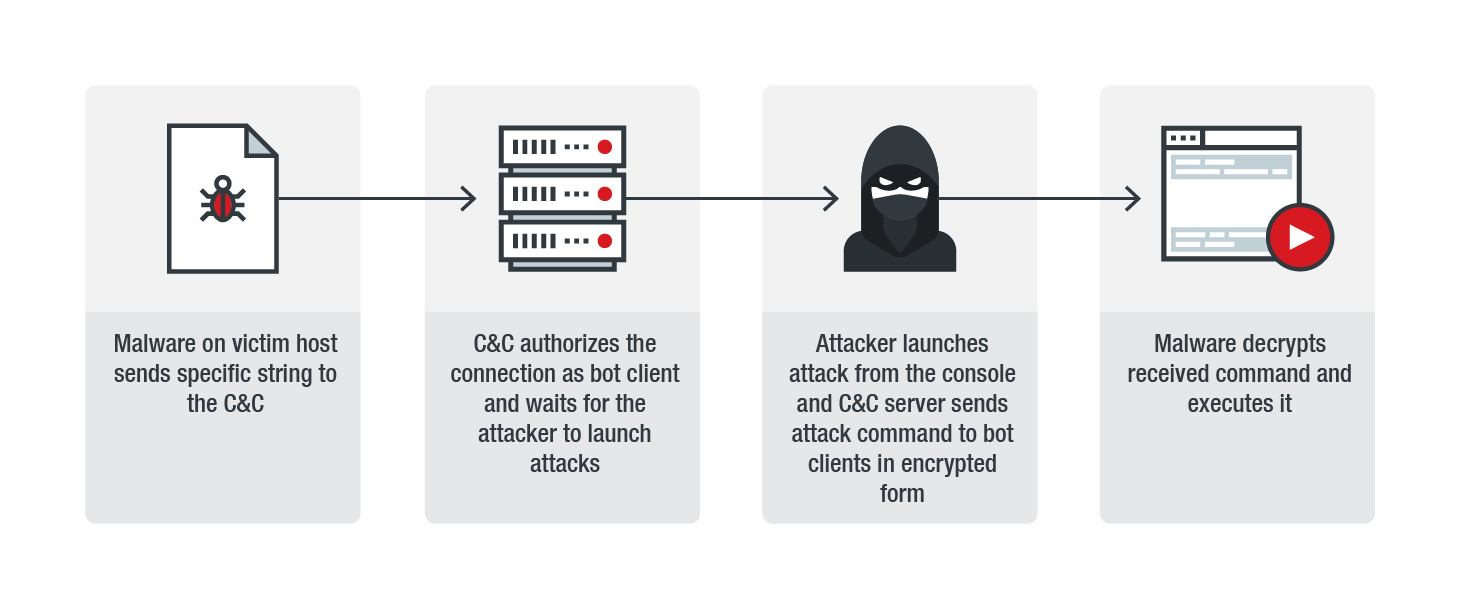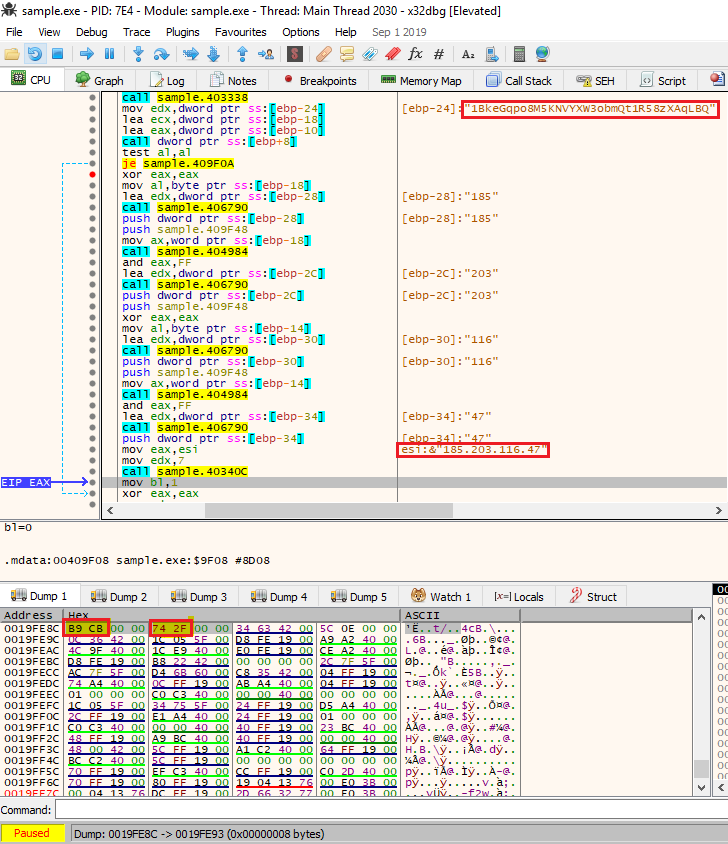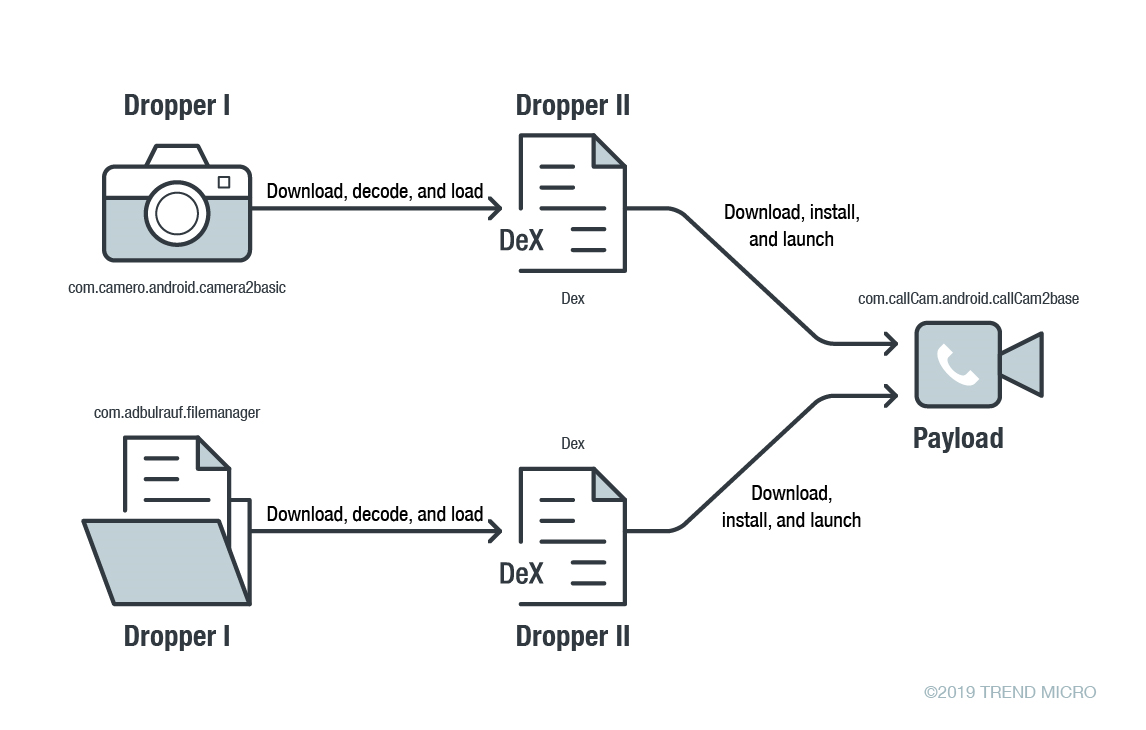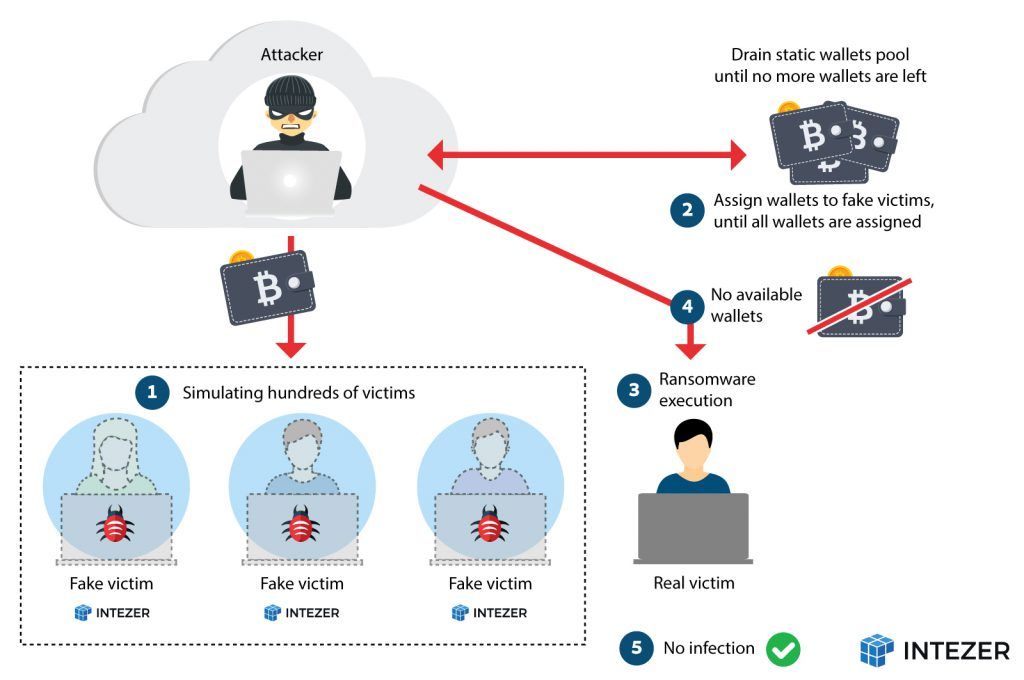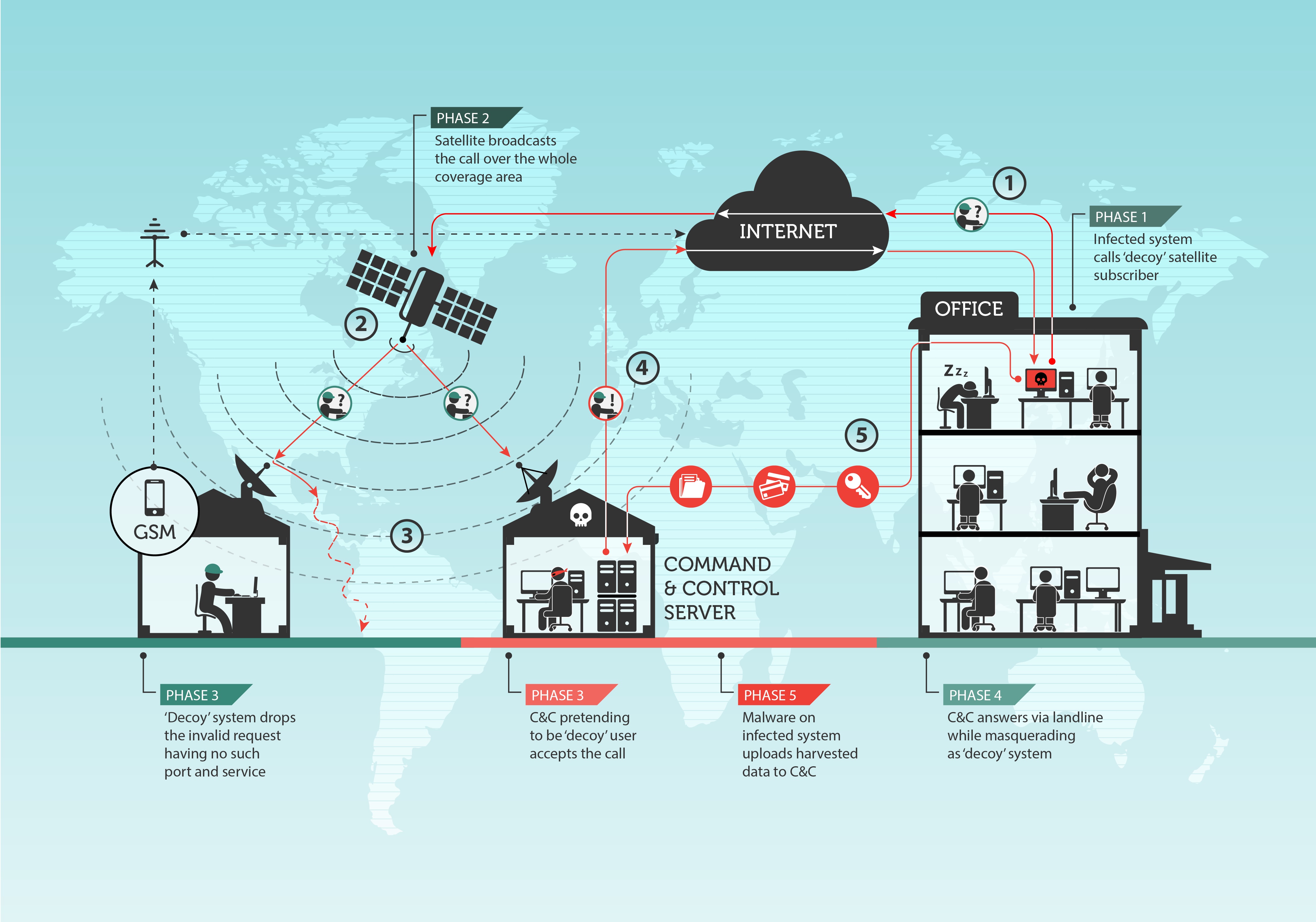
Turla In The Sky With Satellites: Cyber-Espionage Group Hides C&C Server Locale IT Voice | Online IT Media | IT Magazine

Glupteba Campaign Hits Network Routers and Updates C&C Servers with Data from Bitcoin Transactions - ThreatRavens
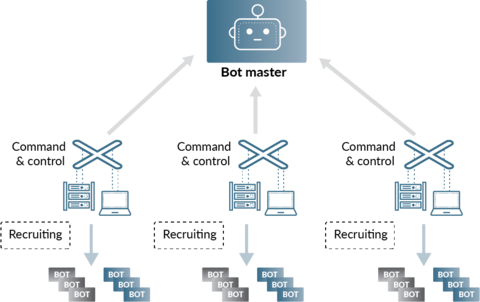
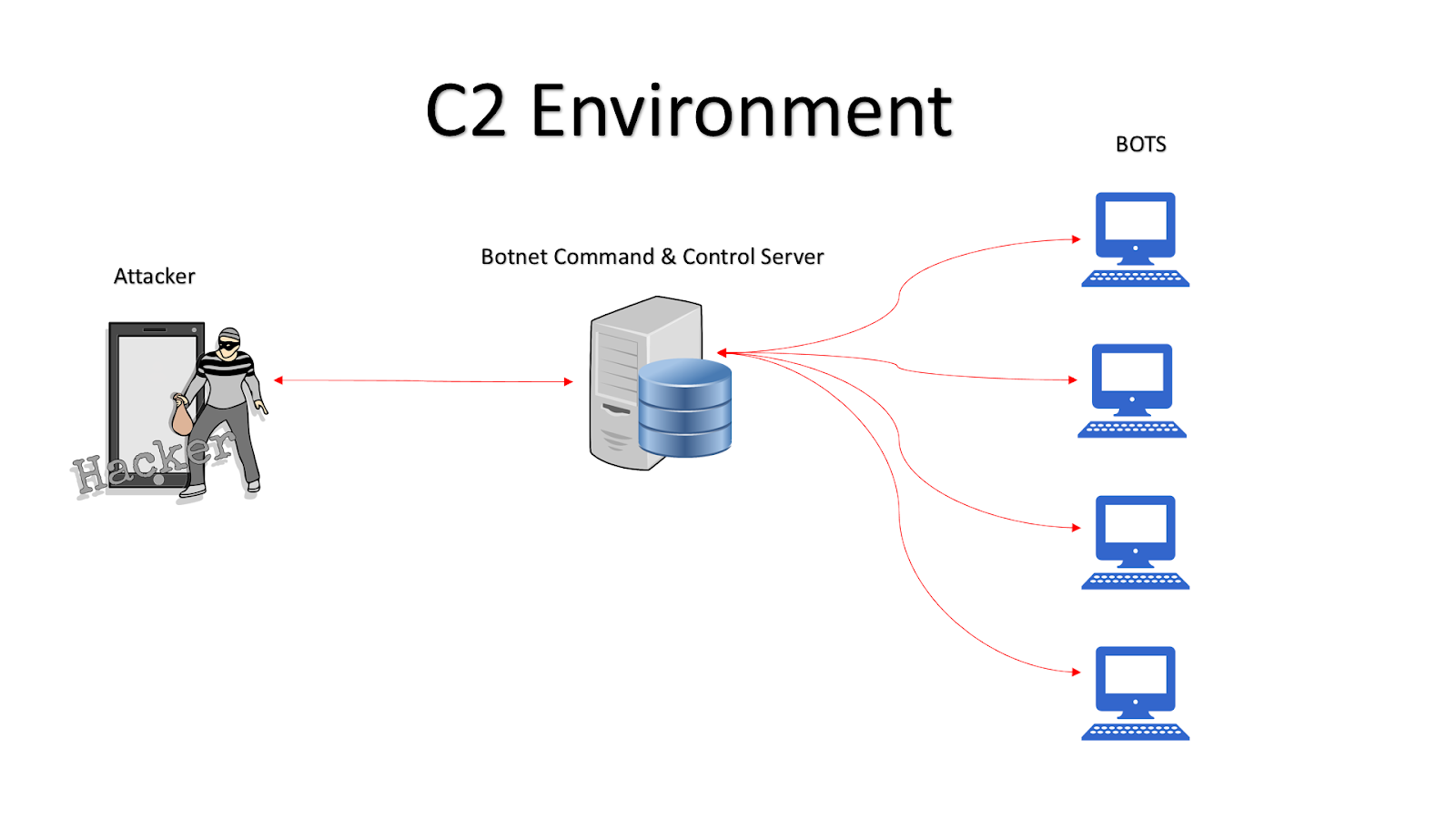
Basic entities of botnet: bots, command and control (C&C) server, and... | Download Scientific Diagram