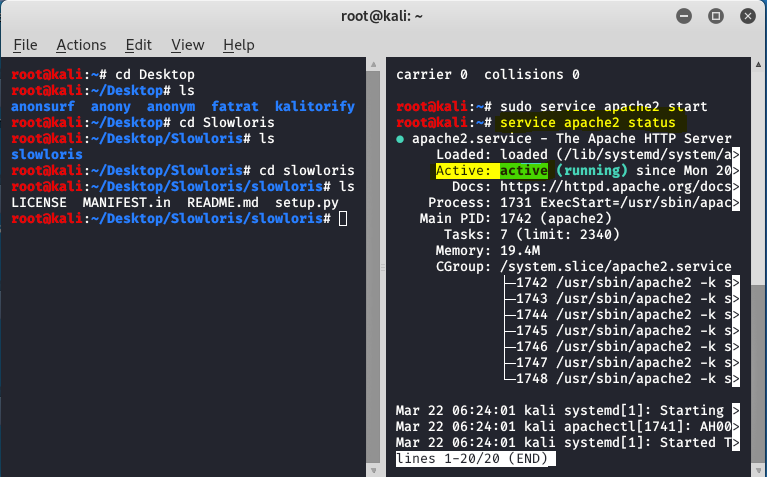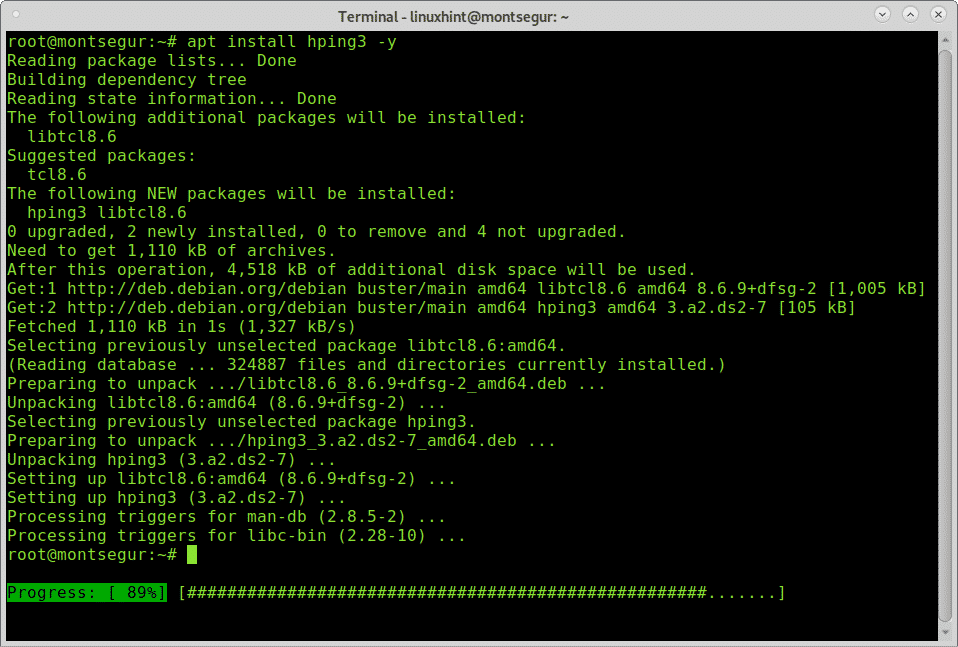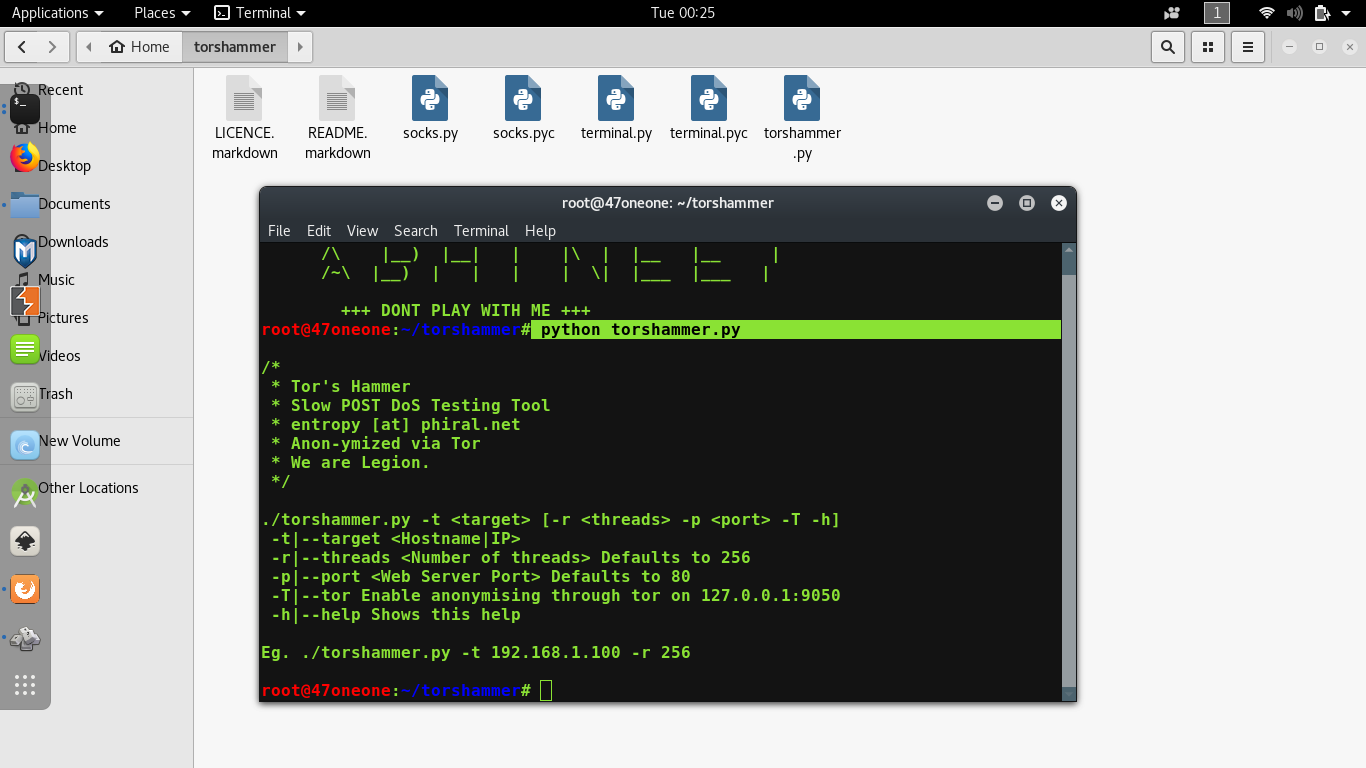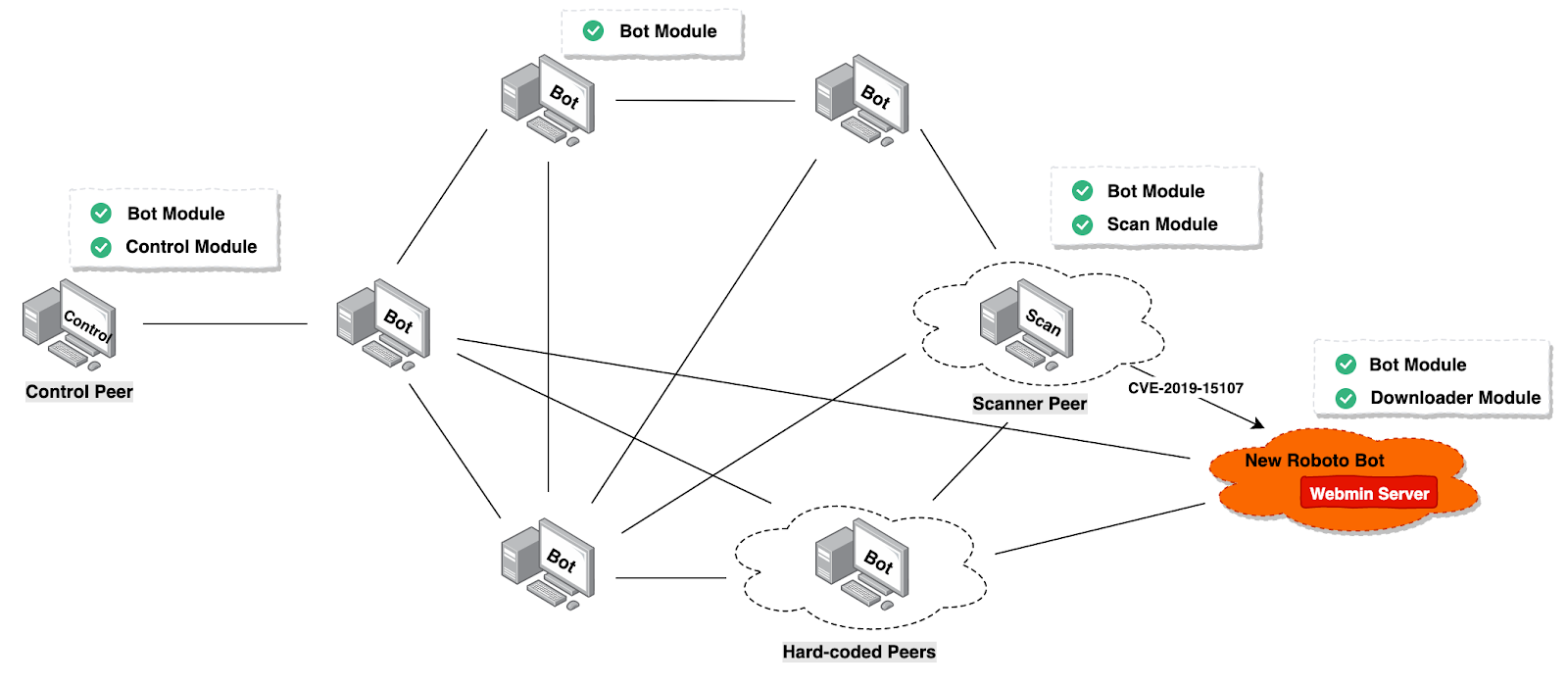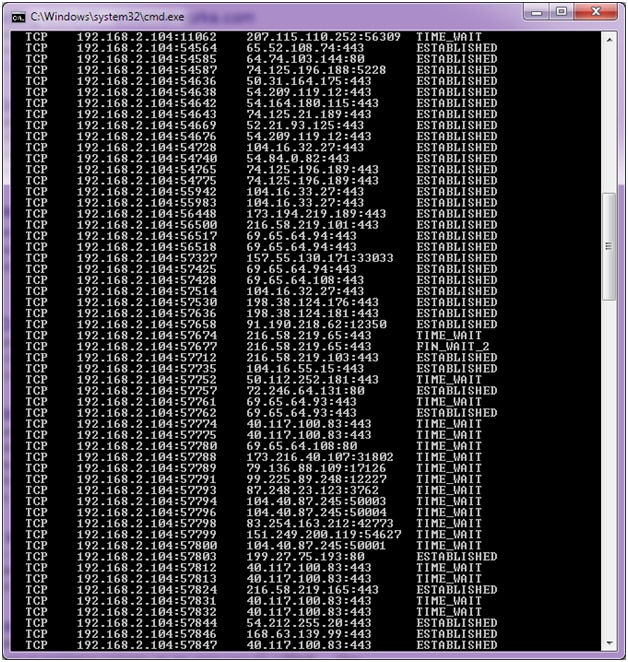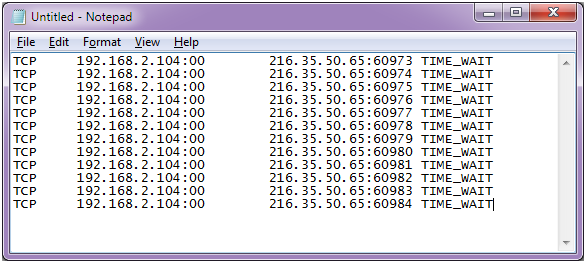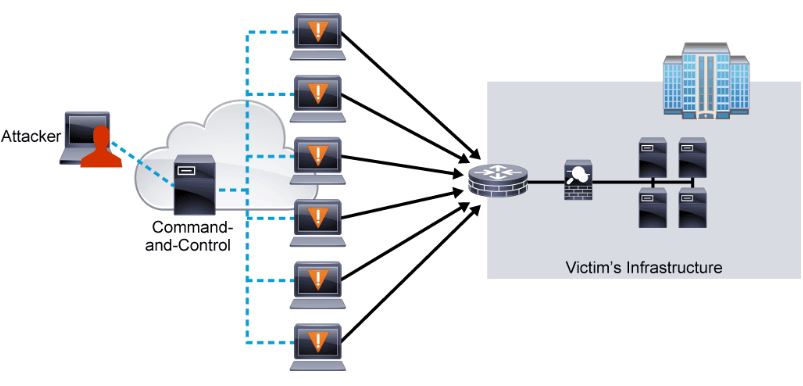
DoS and DDoS attack-The Ultimate goal for CCNA, Cisco Networking, Cisco Certification Exam, Linux Installation and Server Management
A simplified model of a botnet conducting a DDoS attack. Once an army... | Download Scientific Diagram
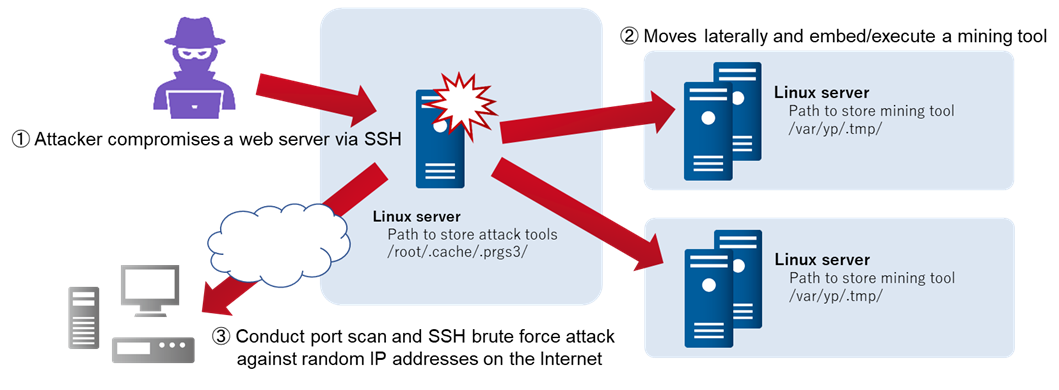
Attacks Embedding XMRig on Compromised Servers - JPCERT/CC Eyes | JPCERT Coordination Center official Blog